After Xu Yuyu, Telecom fraud related topics for discussion of the heat continues to rise. Kcon Conference last weekend, Telecom fraud Only_guest Hat PKAV with years of experience to share related issues, in addition to case studies, Lei Feng also excerpts from several of you about Telecom fraud "cold knowledge".
1. Telecom scam profits much higher than operators
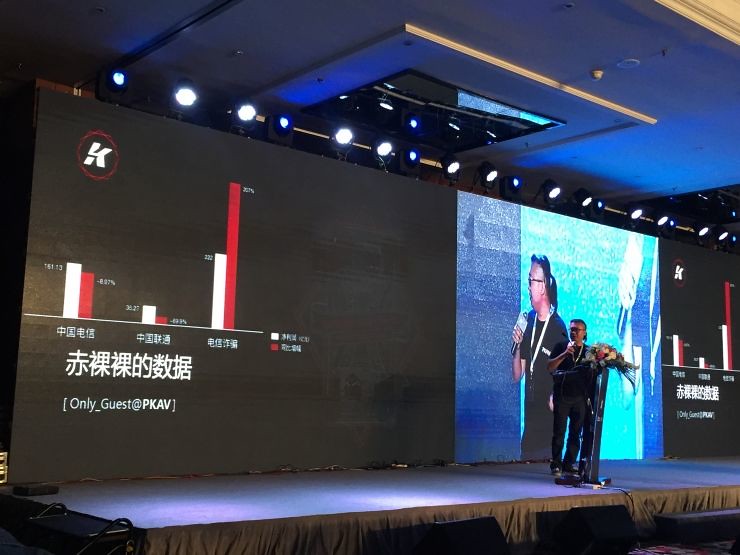
Chart data from speakers at Only_guest's circle of friends. According to Only_guest introduction, two months ago, a friend of the Bank in his circle of friends to comment saying, China Telecom and China Unicom's total net profit last year, there is no sum of profit for Telecom fraud this thing higher. Subsequently, the Only_guest found through the survey data in the graph, data shows:
China Telecom's net profit was 16.113 billion yuan last year, rose-8.97%
China Unicom's net profit last year was 3.527 billion, rose-69.9%
Telecommunications fraud last year's net profit of 22.2 billion, growth of 207%
This group of naked figures irony, but also exposed the huge Telecom fraud industry interests.
2. even if the caller ID is 110, also has the potential to be a liar
Only_guest described in his speech, repertoire there are basically two kinds of Telecom fraud, is a pseudo-base station by sending fraud messages via VoIP fraud phone calls. Regardless of the crooks come up with clever tricks to achieve channel is basically two.
Pseudo or false base station the base station, generally by the host and portable computer, easy to carry, to carry all equipment in a backpack, so liquidity is strong. Carrying a fake base station crook just like guerrilla with a backpack, a day for a place, a person can be a team.
VoIP Internet phone, VoIP technology is mainly based on traditional analog voice signals are digitized, compressed, packaged, encapsulated into a frame and a series of processing, voice services can be hosted through the IP network. VoIP services can be used between VoIP users, but also phone calls and phone users, such as the use of traditional fixed-line network as well as users of wireless mobile networks. Con artists use this technique, you can change the display number, calling number 110, also has the potential to be a liar, and difficult to trace them.
Although relevant departments as well as operators of pseudo-base station VoIP can change the display number limit is not allowed into public security departments or agencies such as the number of the Bank, but Only_guest told net of Lei feng, to remedy this limitation is not high technical threshold.
3. each scam after "private custom"

In his speech, Only_guest shares a common case of operation. Through case studies, we can put the whole fraud process is divided into three parts.
A first step, the selected victims. Before the implementation of fraud, liar will first be selected information and background images of victims. Priority will usually choose a certain social status and assets to start. Vans case
The second step, custom routines. According to selected victim information, carefully customized cheat will cheat tool. Whether through link to open a page or a phishing site, fill in the form and download control is based on a real Web site with good control of imitation or modification. Victims are not aware of anything unusual.
The third step, started cheating. Process cases:
Cheats call of the victims, said authorities issued an arrest warrant for you, and put all your assets are frozen, and then a link to the victims, is customized website link page, with relevant departments of the site looks almost identical to warrant a page all accurate information about victims or case number is true.
When the defrauding victims of success trust, will help thaw the asset on behalf of the victims to fill out a form of asset liquidation, including account information, online banking payments to victims, as well as auxiliary tool, is a dynamic password card or USB.
Complete the form to fill out, cheats will let you download a similar to things like online banking security controls, click on the link, cheat will directly through the black screen to connect directly to control the victim's computer. (Black screen connection is, the other party in connection to control your computer, will not normally be perceived. )
When crooks use the form and complete the transfer of information in the computer steps will tell you on the phone, make sure you tell your press the OK key on the USB part, dynamic password or read to him. To complete this last step, the victim card that all the money will be transferred.
4. before the deception, turn to the Red Cross for a dollar
Only_guest told of Lei Feng network (search for "Lei feng's network", public interest), found in the tracing investigation of their case, in order to evade arrest as far as possible, reduce the cost of fraud, fraud rings usually have an overseas or Taiwan city, IP and IP. Overseas or Taiwan IP transfer or money-laundering, city, IP make a specific fraud task distribution, distribution of subordinate uses pseudo-base station to send text messages or call using VoIP Con staff.
When the track, Only_guest also found that overseas or Taiwan, two different IP addresses fraud ring would occasionally get together for "industry" or help each other money-laundering. Each other communicate in jargon, such as "washing the car" or "car wash" is money washing or washing money. Vans iPhone case
There is an interesting detail, in their tracking of Taiwan in the fraud ring, found a group of people, at the time of each transfer of victims, will be transferred to the Red Cross Foundation 1 money, then the victim card balance transfer to their accounts. For this specific reason is not known, either transfer the operation and are comfortable doing, funny and ironic.
5. "inner demons" is the backbone of the information leakage
Telecom fraud ring, the first step is to obtain personal information. In addition to black, fraud ring gets personal information sector, including telecom operators, courier companies, and even some government departments ' staff. 26th media has reported, a staff member Shun Feng express company in Hunan, was accused of crime of infringing upon citizens ' personal information, to sell the system account password to others, led to a lot of personal information disclosure.
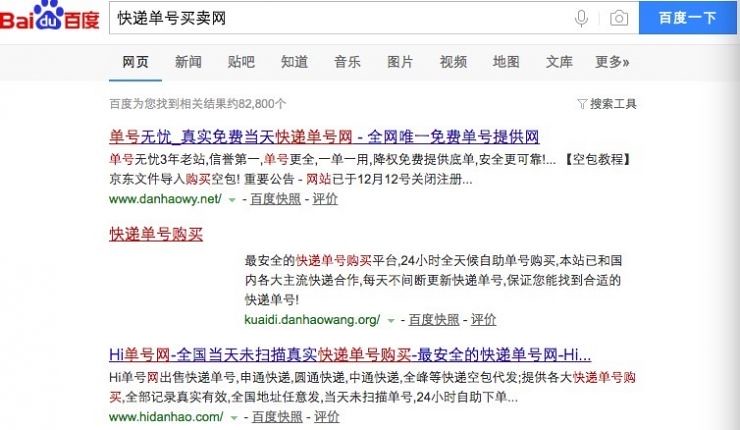
In fact, according to public disclosure of judicial instruments, similar to the "Shun Feng inner demons" sell customers ' personal information is not uncommon. Through QQ search simple groups, the Group found more than one that shows sales information, in addition to SF, there are several other courier companies. To express a single buying group announced that single 3.5 Yuan each, a large quantity of Cong, 50 single purchase buys 300 single price discount for 3. Sold through Baidu search, there will be a number of related information, and even there you can extract single information transactions.
Not on Telecom fraud known as "cold knowledge" there are many others, this has great interests there are quite a few practitioners of the industry chain to play. Xu Yuyu event is not case, hopes hot later, there'll be fewer victims.

No comments:
Post a Comment